IT configuration
Proxy parameters for organizations
⚠️ The following is intended for IT departments ⚠️
If your organization requires a proxy to allow Dilato to connect to the internet, follow these instructions. You may want to install Dilato using GPO before setting up the proxy.
Table of contents
- Setting Proxy Parameters
- Whitelisting Dilato servers
- Using MITM-style proxy
- Authenticating with the proxy server
- Testing connections with proxy
Setting Proxy Parameters
Starting with Dilato 1.44.0, the app automatically uses operating system proxy settings and no additional setup is required. Note, that the proxy server must support HTTPS traffic.
Use operating system settings (default)
Refer to official guides for setting OS-level proxy:
- for Windows: https://support.microsoft.com/en-us/windows/use-a-proxy-server-in-windows-03096c53-0554-4ffe-b6ab-8b1deee8dae1,
- for macOS: https://support.apple.com/guide/mac-help/change-proxy-settings-on-mac-mchlp2591/mac.
You can also set the DILATO_PROXY environment variable value to system to force its use of the OS proxy settings (default behavior).
Use direct connections
If you want to force the app to use the direct connection (bypassing the OS proxy), set the DILATO_PROXY environment variable value to direct. Restart the app for changes to take effect.
Use different proxy server than the OS
If you want to force the app to use a different proxy server than the one specified by the system settings, set the DILATO_PROXY environment variable value to https=<host>:<port>.
Example:
DILATO_PROXY="https=127.0.0.1:8080"
DILATO_PROXY="https=socks4://127.0.0.1:8080"
DILATO_PROXY="https=socks5://127.0.0.1:8080"
Restart the app for changes to take effect.
You can verify in app settings the configuration did take effect:
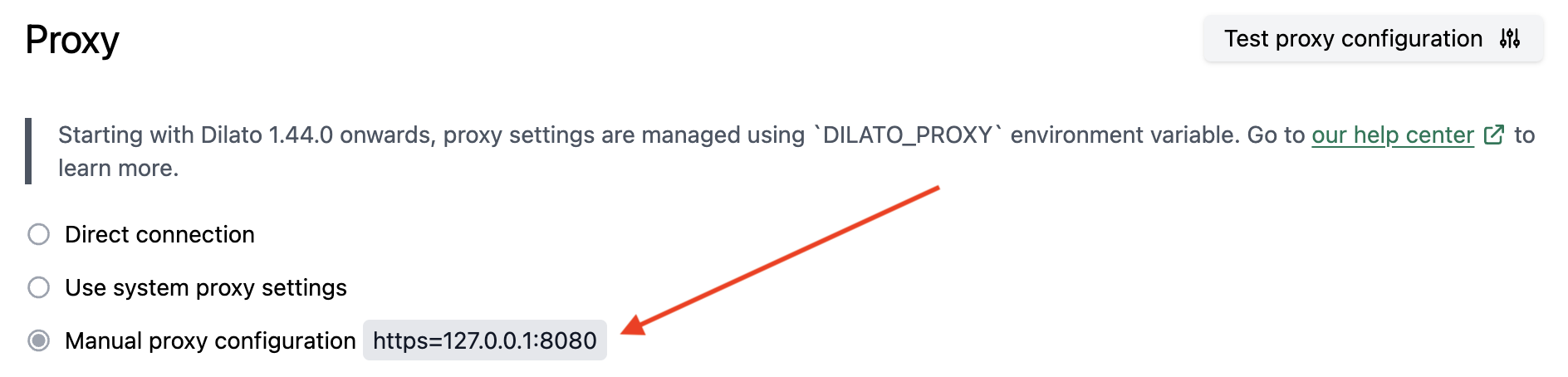
Whitelisting Dilato servers
If your proxy blocks all servers by default, make sure you allow Dilato domains:
ALLOW *.dilato.app
Authenticating with the proxy server
If your proxy server requires authentication, NTLM authentication is supported.
The server host must be allowed by the Windows Zones Security Manager (queried for URLACTION_CREDENTIALS_USE). By default, this includes servers in the Local Machine or Local Intranet security zones. This behavior matches Internet Explorer, Microsoft Edge, and other Windows components.
Using MITM-style proxy
As of today, Dilato supports MITM-style proxy. However, in the future, we are planning to stop supporting this kind of proxy and use certificate pinning with our servers. This means, only pass-through proxies will be allowed in the future. If this affects your organization, please contact us at info@dilato.app.
To use a MITM-style proxy you must install a CA certificate in the OS trust store for HTTPS traffic to work with your proxy server.
Testing connections with proxy
Go to the app settings, scroll to the Proxy section and click Test proxy configuration. When you get "Configuration is correct", the app could successfully connect to Dilato servers over HTTPS.
Troubleshooting
- Verify in app settings that the correct mode is selected (direct, system, or manual).
- Make sure the host and port are input correctly:
- If you are using system settings, in the operating system settings,
- If you are using manual settings, in the Dilato app settings,
- Ensure that no firewall or antivirus is preventing Dilato from connecting to its web servers,
- Verify Dilato servers are allowed.
- (if using MITM-style proxy) Verify correct CA certificate is installed in the OS trust store.